Table 1 (Forbes.com)
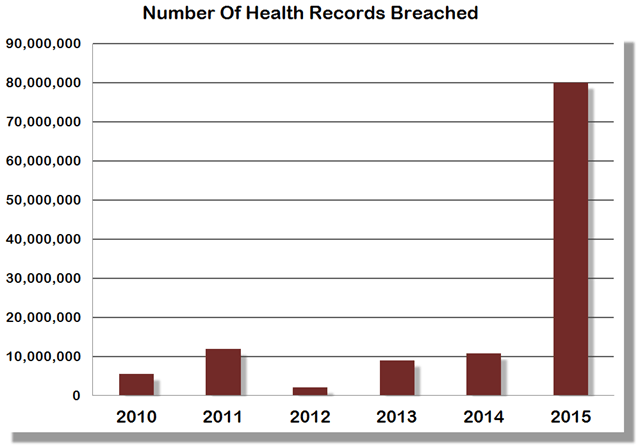
In 2015, data breaches in Healthcare totaled over 112 million records, according to an article recently published by Forbes. According to the Office of Civil Rights (OCR), which published data breaches as reported to them and required by HIPPA, there were 253 healthcare data breaches that affected at least 500 individuals, with a combined loss of over 112 million records in 2015.
The bottom line? Healthcare data breaches are a massive threat to health systems and organizations, and many organizations have been struggling to find ways to protect themselves. Daniel Berger, president and CEO of Redspin, a healthcare security consulting business, says that protection starts with your employees.
“At the end of the day, your ultimate goal is to get your employees to believe that patient health information is part of their responsibility, their civic duty, so to speak,” said Berger in an interview featured in a recent Healthcare IT News article. “They need to look beyond, ‘here’s our policy,’ to adopting a personal stake in keeping patients records secure.”
Companies with a bring-your-own-device (BYOD) policy are at a higher risk because, you can create any policies you want, but employees are far more likely to download patient’s personal health information on their own devices to take home. The problem arises when laptops get stolen or lost, putting patients’ personal data and well-being at risk. Along with ensuring employees use company monitored and sanctioned devices, ensuring there are ample network security measures in place to protect against external threats is also essential. Below, you’ll find 5 strategies for protecting against potentially debilitating healthcare data breaches.
1. Consider Conducting a Risk Assessment
Conducting an annual HIPAA security risk analysis is a requirement of the HIPAA Security Rule, so it is best to plan it in advance and make room in your budget for it. There are countless changes that take place over the course of a year, including “new system deployments, IT infrastructure enhancements, organizational restructuring and employee turnover,” according to Healthcare IT News. When you consider all of these changes, it leaves a lot of room for new vulnerabilities to arise. Because IT circumstances fluctuate so rapidly, it’s critical that you schedule regular risk analyses.
2. Implement Data and Hardware Encryption

It’s best to insist on encryption of data and hardware devices, especially when it comes to portable devices. Data encryption is considered a key way of preventing data breaches. When we refer to encryption, we are essentially referring to the translation of data into a secret code that requires a username and password to gain access to the decrypted data. According to Healthcare IT News’ fourth annual Breach Report, encrypting laptops and other portable devices has been their top recommendation every single year. “From 2009 to the present, the loss or theft of unencrypted portable devices have made up over a third of all large breach incidents and impacted over 50 percent of health record put at risk,” the report reads.
While there are certainly hurdles to overcome when it comes to encryption, including budgetary constraints, user-training needs and employee resistance (to name a few), the cost of implementation pales in comparison to the pain that comes with a major beach incident due to the loss of an encrypted device full of private health information, according to Healthcare IT News.
3. Conduct Frequent Vulnerability and Penetration Assessments
While threats from hackers and other malicious outsiders it not the leading cause of healthcare data breaches, they are predicted to become a much larger threat in years to come. Hackers have the potential to cause considerable problems for the healthcare industry. While hacking breaches haven’t been widespread, Healthcare IT News’ report notes that the 12th largest breach of all time was the 2012 hacking incident at the Utah Department of Health, in which 780,000 patient records were affected. The report backs up the claim that hacking incidents will increase.
The reason for this, according to the report, is that “personal health records are high value targets for cybercriminals, as they can be exploited for identity theft, insurance fraud, stolen prescriptions and dangerous hoaxes.” In addition, many health providers process and store credit card information.
Successfully guarding against these types of threats requires ongoing “vulnerability scanning and remediation.” A best practice is to implement a monthly, quarterly, or annual test schedule so that results may be compared and opportunities to improve network and patient data security may be revealed. Along with this, external and internal penetration testing is also a good idea. “These types of tests more closely mimic the paths of malicious attackers and can often expose interrelated weaknesses that would be beyond the scope of typical vulnerability assessments.”
Healthcare IT Security Predictions for 2016
Forbes called 2015 “the year of the healthcare data breach” (Table 1), with multiple organizations falling victims to malicious attacks. One organization, Anthem, was breached due to phishing attacks, which proves that oftentimes people are still the weakest link in terms of network security. If there is one thing you should take away from this post, it’s that no matter how strong your security measures are, you employees absolutely need to be properly trained on how to protect data and why it is critically important to do so. Garry McCracken, vice president of technology for WinMagic, predicts that “2016 will see a ‘back-to-basics” approach where health care organizations push hard on training workers to take the preventative measures necessary to avoid more breaches in the future. While 2015 wasn’t the best year in terms of healthcare data protection, with the amount of research and analysis currently being done, there is great home for improvement in 2016.
Is your organization protected?
Get in touch with us today to get started.
Image Credits: forbes.com
